32+ next generation firewall diagram
The main fuse box also known as the Power Distribution Module or PDM is located under the hood on the left front fender just ahead of the bulkhead moduleThe fuses in the main fuse box are paddle type mini fusesThe battery power fuses located next to the batteries are screw-in mega fuses. A computer is a digital electronic machine that can be programmed to carry out sequences of arithmetic or logical operations computation automaticallyModern computers can perform generic sets of operations known as programsThese programs enable computers to perform a wide range of tasks.

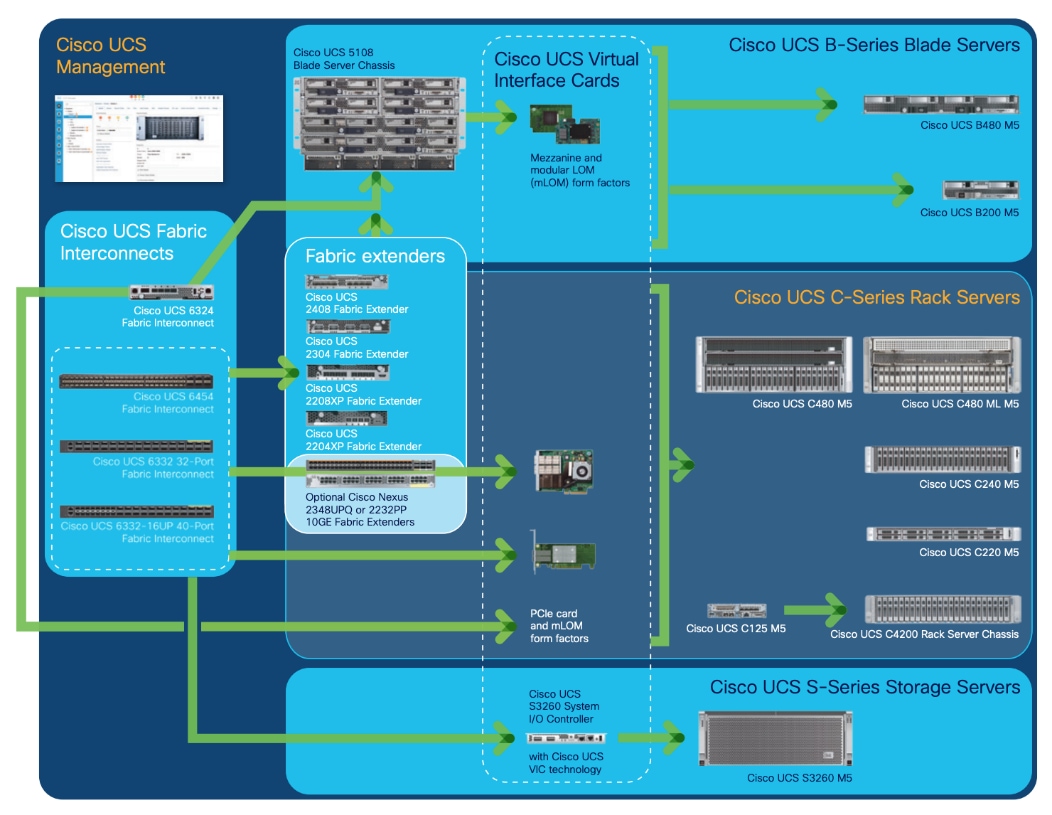
Cisco Data Intelligence Platform On Cisco Ucs M6 With Cloudera Data Platform Private Cloud Cisco
This column lists the current IP addresses of the gateways hosted on the latest generation of hardware.

. Connect with the VPN Client. Emerging technologies are characterized by radical novelty in application even if. Where the first 3 represent the OUI the next three represent the NIC.
Also intrusion prevention system or IPS is a device or software application that monitors a network or systems for malicious activity or policy violations. O A relay forwards messages accepting messages from originators or other relays and sending them to collectors or other relays. We will guide you on how to place your essay help proofreading and editing your draft fixing the grammar spelling or formatting of your paper easily and cheaply.
In the given scenario Loopback0 222232 is advertised into OSPF. Refer to Cisco Secure PIX Firewall 6x and Cisco VPN Client 35 for Windows with Microsoft Windows 2000 and 2003 IAS RADIUS Authentication for more information on remote access VPN configuration for PIX 6x. 192 IPv6The Next Generation Internet Important.
This type provides access to an enterprise network such as an intranetThis may be employed for remote workers who need access to private resources or to enable a mobile worker to access. The firewall can block certain Web-oriented cookies Java scripts and pop-up windows. The basics of IPv6 are similar to those of IPv4 -- devices can use IPv6 as source and destination addresses to pass packets over a network and tools like ping work for network.
RFC 6749 OAuth 20 October 2012 G The client requests a new access token by authenticating with the authorization server and presenting the refresh token. Rental price 70 per night. Choose Common security groups then choose Next.
The main differences between the three Trust Platform tiers include the level of involvement you have in choosing or defining a secure element configuration for your use case deciding what credentials you want to provision and selecting the Minimum Orderable Quantity MOQ that will best suit your project requirements. Virtual private networks may be classified into several categories. If your network has a firewall that filters queries from local DNS servers youll also need to configure a server.
Which device will issue ARP request. Remote access A host-to-network configuration is analogous to connecting a computer to a local area network. Emerging technologies are often perceived as capable of changing the status quo.
It can also be known as the physical address. IPv6 is not supported by the CTC and IUCV network connections of the IBM Z hardware. View the VPN Client Log.
Must contain at least 4 different symbols. IPv6 Internet Protocol version 6 is a set of specifications from the Internet Engineering Task Force IETF thats essentially an upgrade of IP version 4 IPv4. 0646d Freightliner Fld 120 Wiring Diagram Digital Resources from.
These scripts can apply firewall rules. O An originator generates syslog content to be carried in a message. Next OSPF is redistributed into BGP.
An intrusion detection system IDS. Enterprise resource planning ERP is the integrated management of main business processes often in real time and mediated by software and technologyERP is usually referred to as a category of business management softwaretypically a suite of integrated applicationsthat an organization can use to collect store manage and interpret data from many business activities. Understanding new technologies generation by generation becomes easier and adaptable with the help of the OSI Model.
If you are provisioning a new server we recommend that you open the client-side firewall to allow outbound traffic for the IP addresses listed in this column. Azure Database for MySQL supports an additional connection policy redirection that helps to reduce network latency between client applications and MySQL serversWith redirection and after the initial TCP session is established to the Azure Database for MySQL server the server returns the backend address of the node hosting the. The IP address is a logical network address and is a 32-bit number which is globally unique for each.
In the below diagram all the devices are recently powered up. Emerging technologies are technologies whose development practical applications or both are still largely unrealized. The diagram below illustrates the following steps.
Follow the steps in these sections in order to verify your configuration. The following diagram illustrates the traffic flow. To perform the steps below we set up a single AWS Ubuntu 1804 machine on an m4large instance using its local storage.
Windows 7 or later. Next generation Threat Prevention. To determine the OS and architecture of a PC type systeminfo at a command prompt and review the output next to OS Name and.
Using The Firewall Option 648 Using the Firewall Option Use these instructions to configure the EVW32C firewall settings to control what types of traffic are allowed on your network. A computer system is a complete computer that includes the hardware. 6 to 30 characters long.
Any intrusion activity or violation is typically reported either to an administrator or collected centrally using a security information and event management SIEM system. Get 247 customer support help when you place a homework help service order with us. RFC 5424 The Syslog Protocol March 2009 Certain types of functions are performed at each conceptual layer.
The diagram provides one or two examples for each layer. GPS coordinates of the accommodation Latitude 43825N BANDOL T2 of 36 m2 for 3 people max in a villa with garden and swimming pool to be shared with the owners 5 mins from the coastal path. H The authorization server authenticates the client and validates the refresh token and if valid issues.
O A collector gathers syslog content for further analysis. ASCII characters only characters found on a standard US keyboard. The client authentication requirements are based on the client type and on the authorization server policies.
Enter a policy name. Next with the freezer door open hold down the flapper door on the left hand side to un-block the optics beam More Products Features If the LED lights on the dimmer flickers first check if the lamp is dimmable The problem defective LED light module is on the fridge side located at the top I tried disconnecting power for 5-10 mins I tried. We started an EC2 instance in the public subnet of a VPC and then we set up the security group firewall to enable access from.
If Firewall Manager detects that a security groups exists that allows port 22 access from everywhere except 2030113132 youre notified when Firewall Manager Service marks the resource as non-compliant. These technologies are generally new but also include older technologies finding new applications.

Palo Alto Networks Palo Alto Networks Palo Alto Firewall Palo Alto
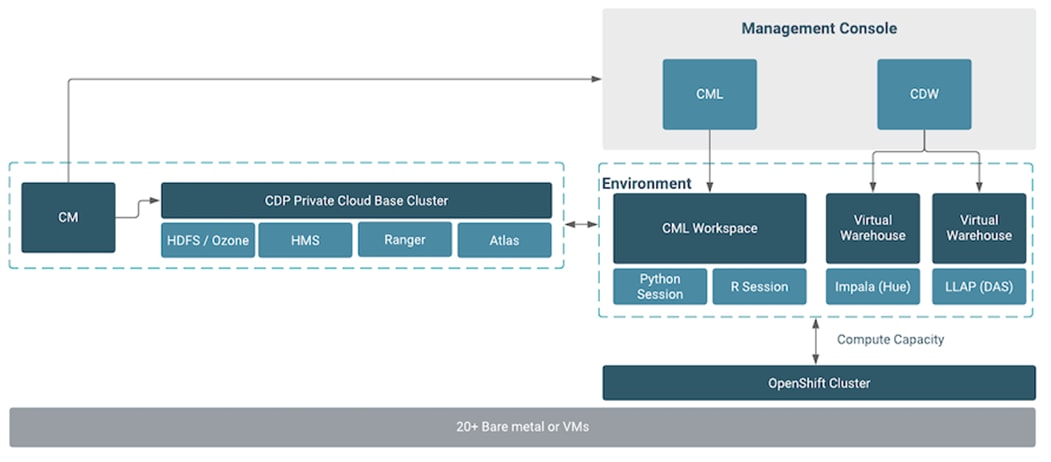
Cisco Data Intelligence Platform On Cisco Ucs C240 M5 With Cloudera Data Platform Private Cloud Experiences Cisco
Cisco Data Intelligence Platform On Cisco Ucs C240 M5 With Cloudera Data Platform Private Cloud Experiences Cisco
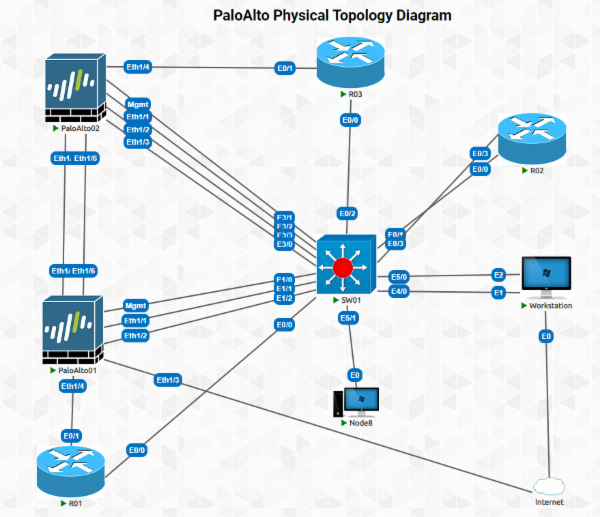
Palo Alto Training

Cisco Data Intelligence Platform On Cisco Ucs M6 With Cloudera Data Platform Private Cloud Cisco

Next Gen Multi Wan Vehicle Gateway Enables 4g Lte Connected Ambulance Security Solutions Ambulance Infotainment

Cisco Data Intelligence Platform On Cisco Ucs M6 With Cloudera Data Platform Private Cloud Cisco

The Art Of Crafting Architectural Diagrams Diagram Architecture Crafts

Converged It Ot Security Gateway To Ensure Critical Infrastructure Protection Security Solutions Smart Building Automation
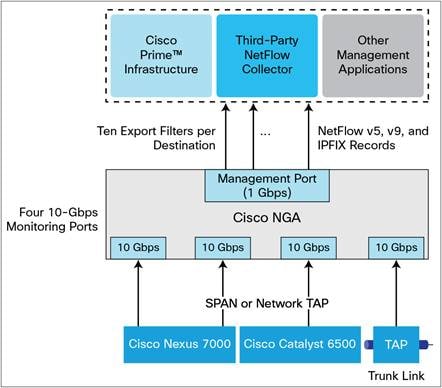
Cisco Netflow Generation Appliance 3340 Data Sheet Cisco

New Lab Topology Firewall Security Ccna Router
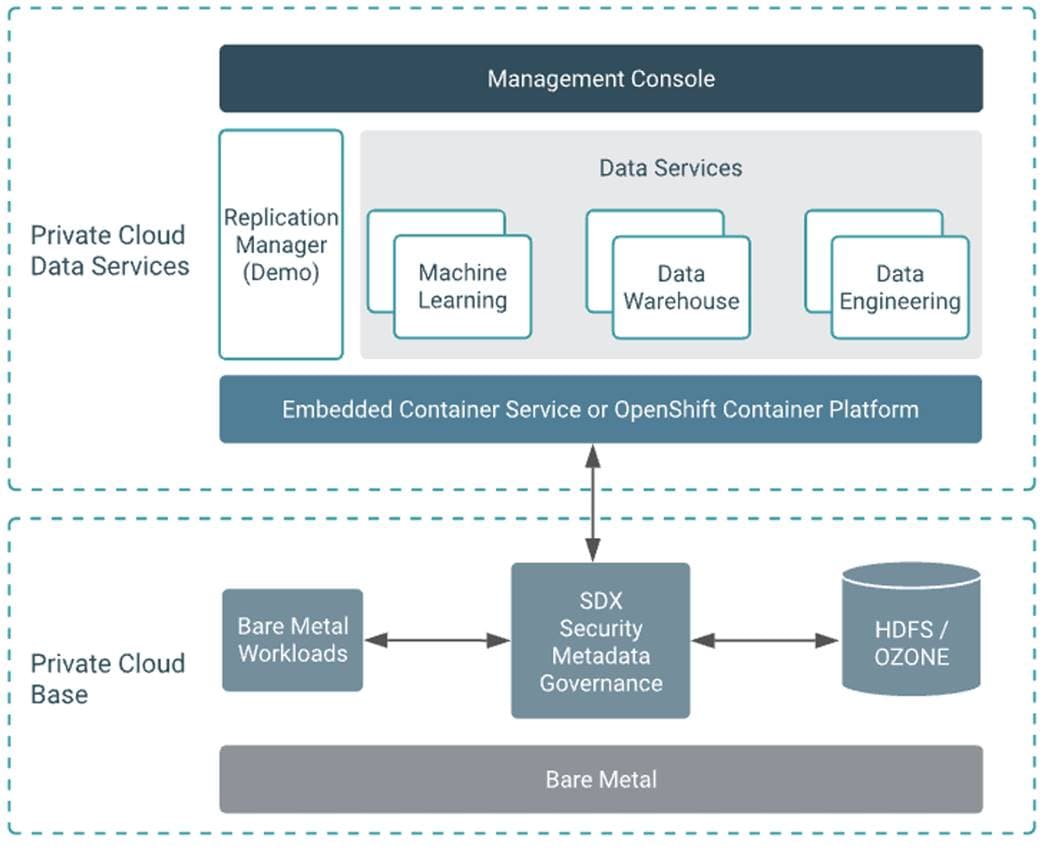
Cisco Data Intelligence Platform On Cisco Ucs M6 With Cloudera Data Platform Private Cloud Cisco
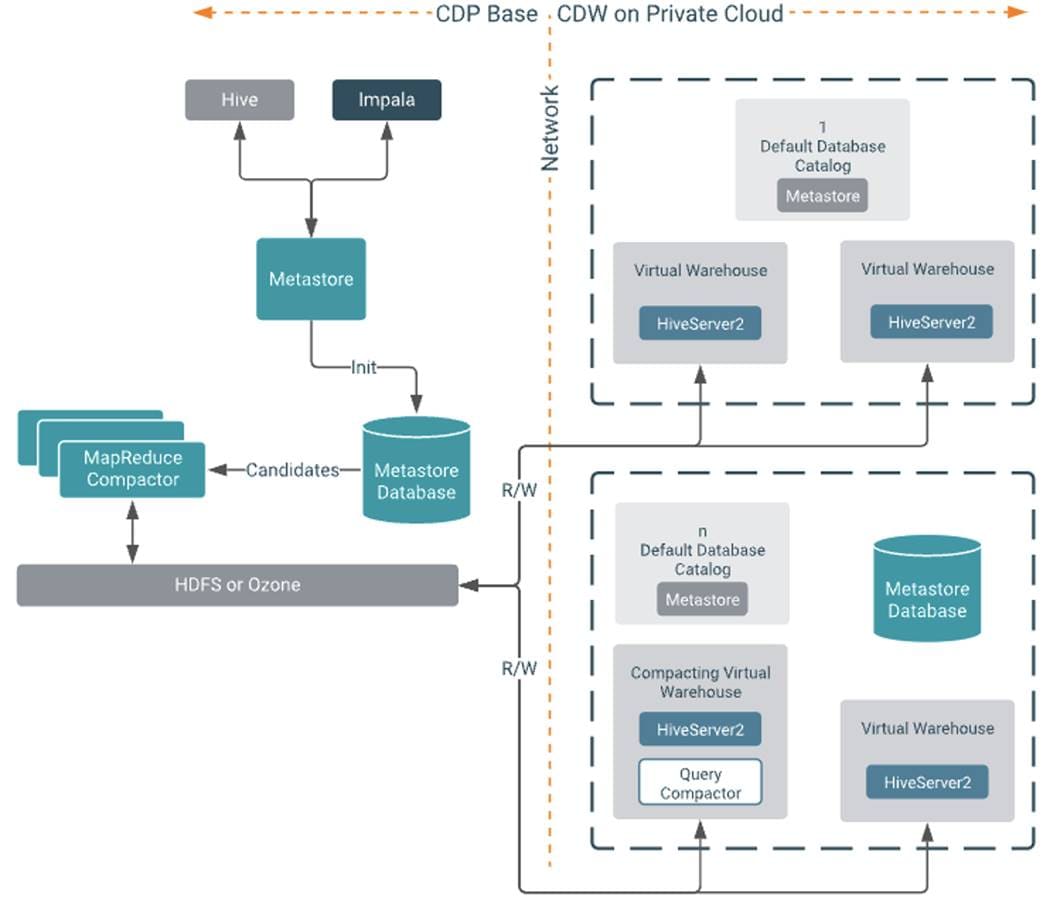
Cisco Data Intelligence Platform On Cisco Ucs M6 With Cloudera Data Platform Private Cloud Cisco

Securing Industry 4 0 Network Infrastructure With Industrial Firewall Network Infrastructure Security Solutions Networking

Cisco Data Intelligence Platform On Cisco Ucs M6 With Cloudera Data Platform Private Cloud Cisco

Amazon Linux Ami Noise
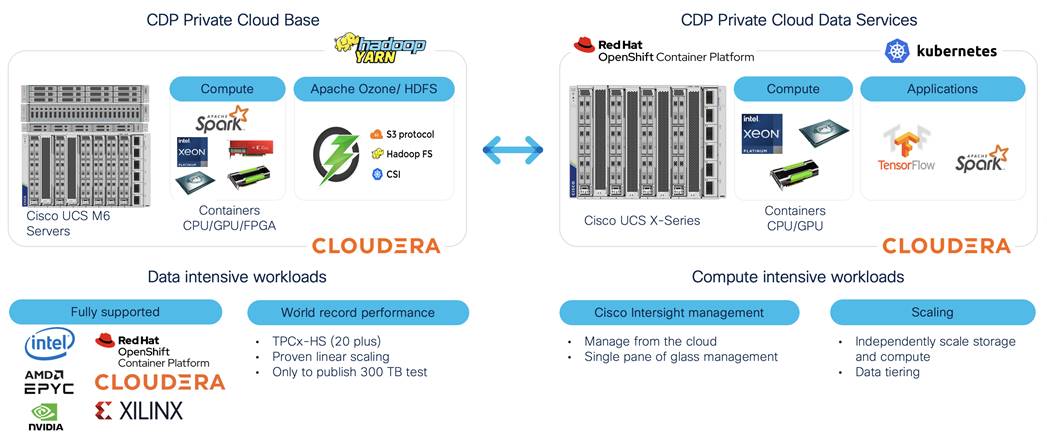
Cisco Data Intelligence Platform On Cisco Ucs M6 With Cloudera Data Platform Private Cloud Cisco